So Nikto!!!
By attempting any of the things listed in this blog post you accept full responsibility for your actions and I will not be held responsible whatsoever. This tutorial is strictly for penetration testers only.
Is your site safe on the internet? Are you sure? Let’s make sure you are safe from hackers. Today we’ll divine into a tool which will help us to stay safe. The name is Nikto. It is a web vulnerability scanner else can be called as a security testing tool that scans web servers for vulnerabilities and other known issues. It’s written in Perl means it will run on most operating systems with the necessary Perl installed. In this nikto tutorial I will guide you through using it on Ubuntu given that Perl comes already installed in Ubuntu. Beauty of open source right? It is very straight forward to use Nikto meaning that from a single command you get whether there are vulnerabilities or not. As they say
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
There are two ways to get started. Let me show you both ways. You can select whichever way you like.
1st Method
Download nikto from the project page. You can list down what are the versions to be downloaded from here. Let’s download using wget.
wget https://cirt.net/nikto/nikto-2.1.5.tar.gz
You can unpack it with an archive manager tool or use tar and gzip together with this command.
tar zxvf nikto-2.1.5.tar.gz cd nikto-2.1.5 perl nikto.pl
2nd Method
Or there is an easy way. Use the below command as usual.
sudo apt-get install nikto
Note
- If you use apt-get you can just use nikto as normal way as shown above.
- If you download and run nikto you always have to be in the nikto folder. Then use perl nikto.pl to execute nikto commands.
Testing/Scanning
Simple Test
As an example we will test this URL.
perl nikto.pl -h http://targetsite.com
or
nikto -h http://targetsite.com
Specifying the test
One of the great things you can do with nikto is to specify the type of checks it runs. So, to only perform an Denial of Service test against your target.
nikto -Tuning x 6 -h http://targetsite.com
See the test types below from the man page.
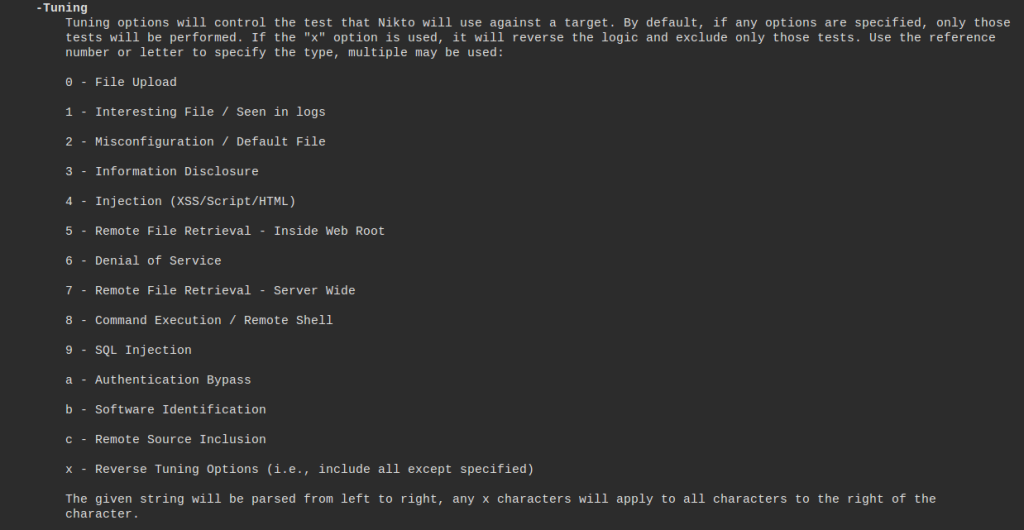
Save results
You can output to a file with the -o option. You can specify the format of the output file with -Format also which is not mandatory.
- csv – Comma-separated-value
- htm – HTML Format
- msf+ – Log to Metasploit
- nbe – Nessus NBE format
- txt – Plain text (default if not specified)
- xml – XML Format
nikto -h http://targetsite.com -o results.txt
Tip & Tricks
1. Anonymous Scanning
If you want to to be anonymous while scanning a particular web for vulnerabilities you can use a proxy server where It hides your IP address and other information. Edit the configuration file for nikto as follows.
vim /etc/nikto/config.txt
Navigate to Proxy settings and change it as follows.
# Proxy settings -- still must be enabled by -useproxy PROXYHOST=85.28.28.209 PROXYPORT=8080
PROXYHOST & PROXYPORT are obtained from a site like this. There are tons of web sites to obtain free proxy servers. Now you can start the scan as follows.
nikto -useproxy -h http://targetsite.com
2. More Information
It might be good to enable verbose output.
perl nikto.pl -Display V -h http://targetsite.com
Check the additional options supported by nikto using the help switch as follows.
nikto -Help
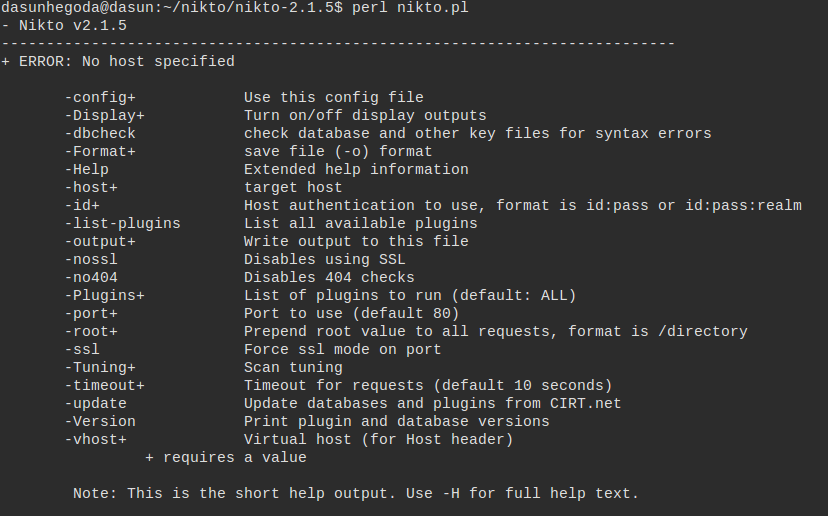
This tutorial would be a good place for you to start. If you like to master nikto use the documentaion. Also note that this will run a ton of http requests that URL specified checking more than for 6500 vulnerabities which can be detected by IDS(Intrusion Detection System). It’s better to have permission to execute tests on a host otherwise you will end up in jail.
If you are really interested in this area you might also want to look at Zed Attack Proxy (ZAP) which is an integrated penetration testing tool for finding vulnerabilities in web applications.
I would like to wrap up the this post with two great quotes on security.
“Companies spend millions of dollars on firewalls, encryption and secure access devices, and it’s money wasted, because none of these measures address the weakest link in the security chain.” – Kevin Mitnick
One more
“If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.” – Bruce Schneier
If you have any questions let me know in the comments below. Your feedback is highly appreciated(happy-face).
![]()



Hey Dasun, Good one !. I introduced this to our company after seen your post. Thanks !
hello if i wanted to get,post or head a html site how should my input be in nikto?
There are tutorials on the web. Please google.
In Test Tuning where you wrote “So, to only perform an Denial of Service test against your target.” do
nikto -Tuning x 6 -h http://targetsite.com
What you are actually saying is that you want to perform all tests against your target, except Denial of Service.
Thank you for the tutorial !