So WSO!!!
By attempting any of the things listed in this blog post you accept full responsibility for your actions and I will not be held responsible whatsoever. This tutorial is strictly for penetration testers only.
Today we are going to talk about a slightly different topic. I’m pretty sure you are going to love it if you are techie like me. This post is strictly dedicated to security personals out there who are white hats(neither black hats nor grey hats). Exploiting a vulnerability is an interesting topic that is also a massive area to be studied. The topic comes under computer security. This blog post will focus on controlling a remote server via a small script which is called a web shell. A popular one has a variation and is known as the ‘WSO Web Shell’. Today we’ll see what we can do with it and how.
So a web shell can also be defined as a type of Remote Administration Tool (RAT) or Backdoor. The web shell can be a full featured administrative GUI which has all the features you need to own/run/destroy a server or as simple as a single line of code that simply takes commands through a browser’s URL and execute it in the server. Beauty is web shells can be written in any language that a server supports. As an example WSO, the one we are going to look at today is written in PHP. So let’s assume that you are running Apache with PHP you will be vulnerable for PHP web shells such as this mighty WSO if you don’t have proper security in place. Most dangerous part is when the shell is installed, it will have the same permissions and abilities as the user who put it on the server. Now you know what’s a web shell is. If you are looking for a list of web shells that are being used in the tech world you can find them right here. Also makes sure that you have harden the Apache server as given this this blog post.
Today we are going to use a web shell call “WSO”. You can download it here. WSO can run under both Windows and Linux, although it has more capability under Linux. Now you might be wondering what are the features it has got and what you can do. These are the set of features which we can use.
- Authorization for cookies
- Server Information
- File manager (copy, rename, move, delete, chmod, touch, creating files and folders)
- View, hexview, editing, downloading, uploading files
- Working with zip archives (packing, unpacking) + compression tar.gz
- Console
- SQL Manager (MySql, PostgreSql)
- Execute PHP code
- Working with Strings + hash search online databases
- Bindport and back-Connect (Perl)
- Brute force FTP, MySQL, PgSQL
- Search files, search text in files
- Support for * nix-like and Windows systems
- Antipoiskovik (check User-Agent, if a search engine then returns 404 error)
- You can use AJAX
- Small size. The boxed version is 22.8 Kb
- Choice of encoding, which employs a shell.
Above list is extracted from thehackernews.com
How To Use
As a penetration tester if you are to exploit your server to make sure that you are safe follow these steps. There is nothing much to be done. See the steps below
- Download the WSO script file from here as just another file and unzip it.
- Identify a vulnerability of the server which you are planning to exploit(with this particular vulnerability you must be able to upload a file into the server). If you missed my last blog post on Nikto which is a web vulnerability find the link here.
- Upload the WSO script file to the server selected via the above identified vulnerability(Note that you somehow have to manage to upload the file via a vulnerability, weak ftp credentials, software errors, etc).
Let’s assume you are able to upload the file with the below given circumstances.
- Site name – abcxyz.com
- abcxyz’s root directory – /var/www/abvxyz/
- Uploaded directory – /var/www/abvxyz/uploads/wso.php
What you have to do now is access the file like this using your favorite web browser. http://abvxyz.com/uploads/wso.php. Then you will be given a screen like below.
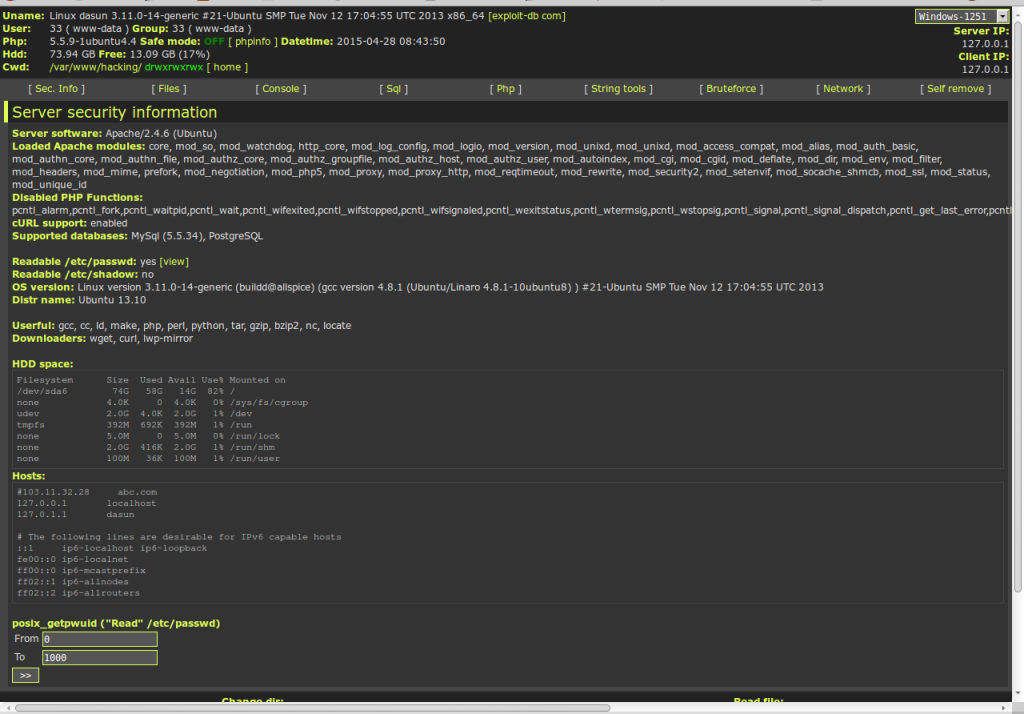
That’s it. Now you own the server like a boss(tongue-out-face).
Tips & Tricks
Let me give you another version of WSO which you can download it here. The difference between the previous one and this one would be when you try to access this file via the web browser it will show you a 404 page. Yep 404. In the 404 page it has a hidden password field waiting for you to enter the password to login to the WSO web shell GUI. Okay I think you got it right. The only difference is this WSO script file is password protected and no one will ever think it’s a web shell because it looks like a 404 page. See the screen shot below.
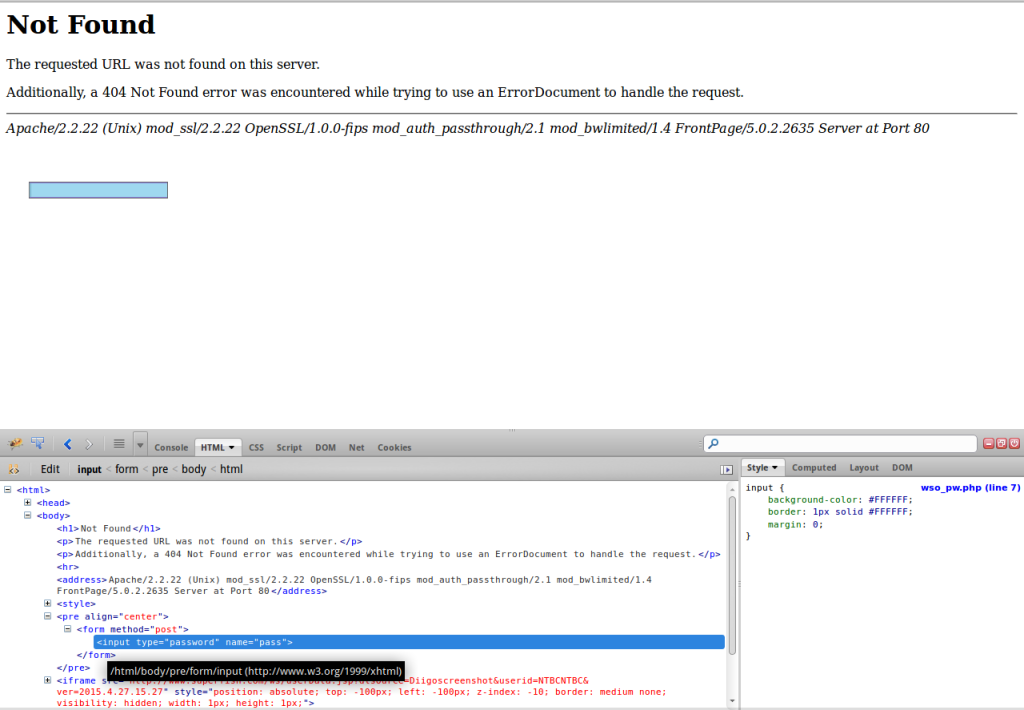
Before you do anything open up the download the WSO script file and set the $auth_pass variable on the top to a md5 value you prefer. It will be used as your password to login.
It’s like you own the server once you have the WSO file in a particular server. You can use all the functionalists given by the WSO script but make sure that you don’t harm anyone. This tutorial is to let the people know that there can be intrusions as shown above. So beware. Keep your applications safe. If you have any questions let me know in the comments below. Your feedback is highly appreciated(happy-face).
![]()




download error